Confidently meet and maintain CMMC compliance.
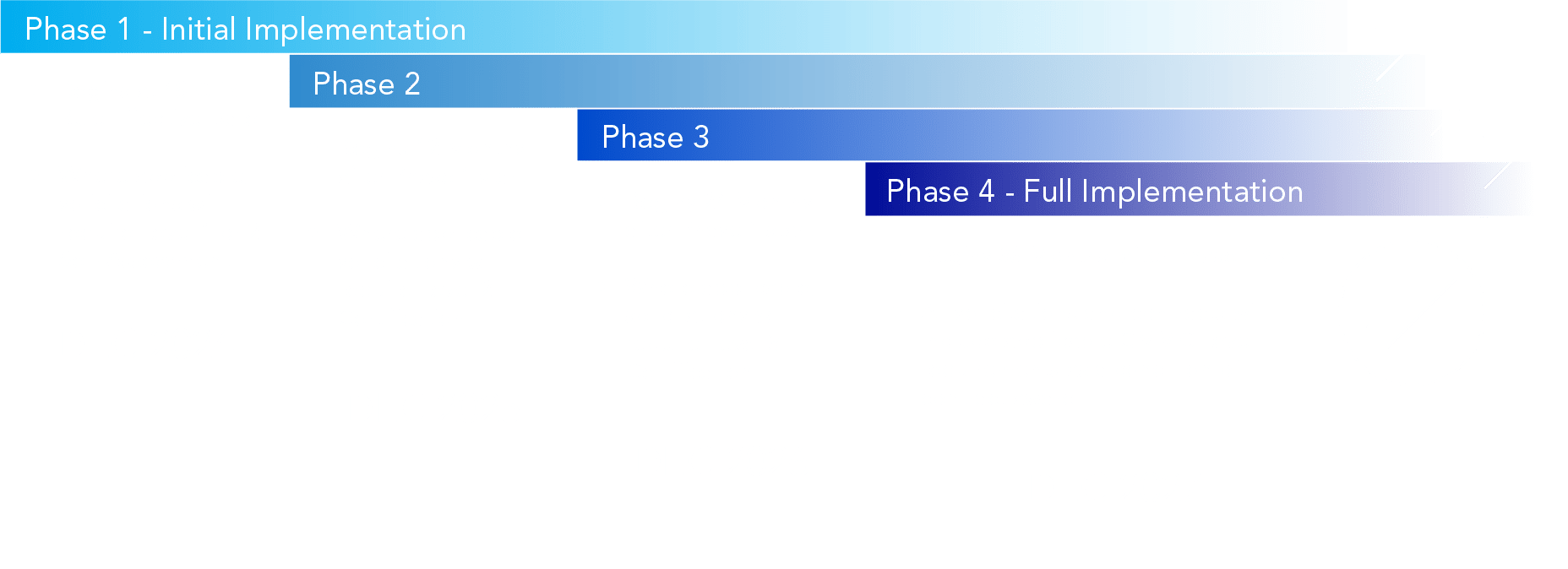
Phase 1 of the CMMC rollout is currently in progress. Abacode can help you prepare for your C3PAO or DIBCAC assessment - without breaking your budget.
How Abacode’s Managed CMMC Program Ensures Your Readiness.
-

GRC Assessment
Find out where your organization currently stands and what security, compliance, and privacy controls you require to meet to reach compliance.
-

Security & Compliance Program Establishment
Get your organization ready for audit and attestation with strategic guidance on implementation of required policies, procedures, and controls.

-

Audit Liaison
Utilize our certified professionals (CISSP, CompTIA Security+, RP, etc.) to validate evidence and communicate with audit and attestation firms.

-

Continuous Security & Compliance Program Support
Manage and report on all compliance initiatives, track progress with our tailored compliance web portal for internal use and external auditor access.

Enabling DoD contractors to confidently meet and maintain a CMMC program and keep their contracts.
Abacode is a fully U.S.-based Managed Security Service Provider (MSSP) dedicated to eliminating breaches and turning compliance challenges—such as CMMC—into competitive advantages. As a Cyber AB Registered Provider Organization (RPO), we help ensure your organization’s audit readiness through a comprehensive program and our team of in-house CMMC experts. We have a diverse clientele with the Defense Industrial Base (DIB): electronics and wiring components, packaging and distribution, mechanical components for aircraft, etc.
Abacode’s managed CMMC readiness program helps you:
Continue business with DoD/prime vendors
Become eligible for new contracts
Meet contractual obligations to protect CUI
Improve security for your organization
Expert guidance from readiness to beyond assessment
Get CMMC Ready with Abacode’s Managed CMMC Service
Enabling federal contractors to confidently meet and maintain CMMC compliance.
Abacode is a Cyber AB Registered Provider Organization (RPO). Our Managed CMMC program will help you build a business case, identify gaps in compliance with NIST 800-171 r2 and prepare you to establish those controls for your company to successfully navigate an official CMMC assessment and maintain compliance afterwards.
Abacode has successfully prepared and navigated CMMC assessments for our clients through C3PAOs and DIBCAC.


Our credentials as a CMMC provider organization
-
U.S. Based Team
100% U.S.-based team, W2 employees.
-
Verified employees
100% E-verified background checks on all employees.
-
RPO
Cyber AB Registered Practitioner Organization (RPO) for CMMC.
-
C3PAO's
Established relationships with top Certified Third-Party Assessment Organizations (C3PAO).
-
GCC High & ITAR
Secure operations within GCC High environment safeguarding ITAR for confident monitoring.
-
Shared Responsibility Matrix
SRM available upon request
-
SOC 2 Type II
SOC 2 Type II certified.
-
ISO 27001
ISO 27001 certified.
-
What is CMMC?
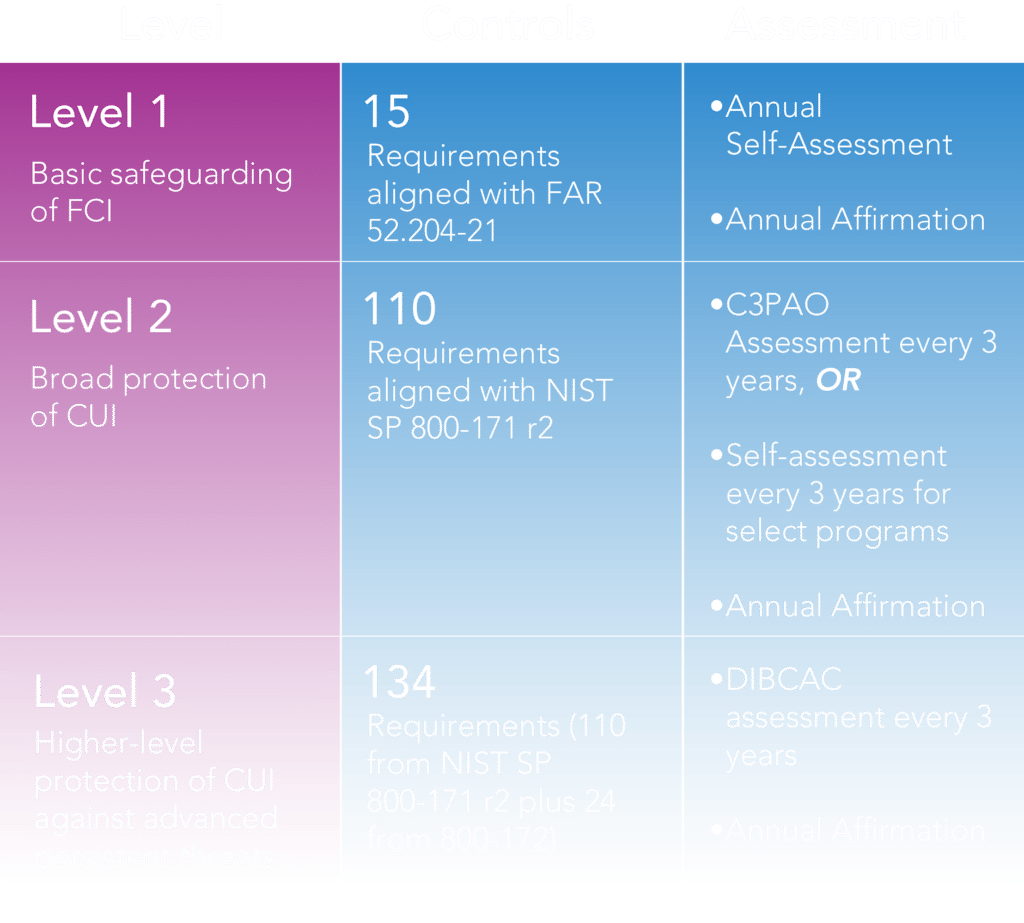
The Cybersecurity Maturity Model Certification (CMMC) is a mandatory framework established by the Department of Defense to safeguard Controlled Unclassified Information (CUI) within the Defense Industrial Base. This program ensures organizations handling sensitive defense data meet specific cybersecurity standards including compliance to the 110 controls of NIST SP 800-171 r2, reducing risks to national security.
-
Why is CMMC Needed?
The CMMC framework addresses the lack of uniform self-governance in cybersecurity across the DIB. With increasing threats to sensitive data, the Department of Defense mandates robust, verified security measures to protect critical information. CMMC certification ensures contractors meet these essential standards, safeguarding national interests.
-
Does My Organization Need to Be Certified?
If your organization contracts or subcontracts with the Department of Defense and handles Controlled Unclassified Information (CUI), you must achieve CMMC certification. Certification is critical for securing and maintaining contracts within the defense supply chain.
-
Problems Facing Organizations
Organizations in the DIB face significant challenges:
- Limited Resources: A shortage of Certified Third-Party Assessment Organizations (C3PAOs) and qualified assessors.
- Time and Knowledge Gaps: Many lack the internal expertise or time to navigate the complexities of CMMC requirements.
- Government Oversight: The need for strict compliance due to failures in self-governance.

The 4 phases of CMMC implementation

The 3 levels of CMMC
CMMC FAQs
What is CUI?
Controlled Unclassified Information (CUI) is sensitive data that needs protection but isn’t classified. This includes things like personal details (PII), proprietary business info, and other crucial government data. Keeping CUI safe is vital for national security and continued government operations. The Cybersecurity Maturity Model Certification (CMMC) helps organizations make sure they’re following the right cybersecurity practices to protect CUI from unauthorized access and breaches.
When does CMMC go into effect?
The Cybersecurity Maturity Model Certification (CMMC) framework is being rolled out gradually with requirements for CMMC already appearing on contracts. Phase 1 of the rollout is scheduled to begin on November, 10th 2025.
The latest news regarding CMMC, can be found on the DoD’s website: https://dodcio.defense.gov/CMMC/About/
It’s best to start working on compliance now to be ready for contract opportunities. Early preparation helps avoid last-minute stress and ensures you stay eligible for DoD contracts. Begin by evaluating your current cybersecurity practices, spotting any gaps, and putting the necessary controls in place to meet the required CMMC level.
What’s the difference between CMMC, DFARS, and ITAR?
CMMC, DFARS, and ITAR all set rules for security and compliance for U.S. government contractors, but each has a different focus:
- CMMC (Cybersecurity Maturity Model Certification):
- Focuses on cybersecurity practices.
- Applies to defense contractors handling Federal Contract Information (FCI) and Controlled Unclassified Information (CUI).
- Ensures organizations meet specific cybersecurity maturity levels to protect sensitive data.
- Requires compliance with NIST SP 800-171 standards for protecting CUI.
- DFARS (Defense Federal Acquisition Regulation Supplement):
- A set of regulations supplementing the Federal Acquisition Regulation (FAR) specific to defense contracts.
- Includes clauses like DFARS 252.204-7012, which mandates safeguarding CUI and reporting cyber incidents.
- Also requires compliance with NIST SP 800-171 standards for protecting CUI.
- ITAR (International Traffic in Arms Regulations):
- Governs the export and import of defense-related articles and services.
- Ensures defense-related technology doesn’t fall into unauthorized hands.
- Applies to any organization involved in manufacturing, exporting, or brokering defense articles and services.
- Requires that protected data doesn’t leave the continental U.S. and is usually accessible only to U.S. persons.
Depending on your contracts and the information you handle, you might need to follow one or more of these frameworks. Knowing the differences helps ensure you stay compliant and secure.
Do I need a government cloud environment for CMMC?
You don’t strictly need a government cloud environment for CMMC compliance, but it is recommended to use a GCC High environment for CMMC Level 2 organizations, especially if you need to comply with ITAR.
DoD contractors must ensure their cloud service provider meets the security requirements for handling CUI as outlined in CMMC. Many providers offer environments designed to comply with federal standards, making it easier to achieve and maintain CMMC certification. Make sure any cloud services used are set up and managed according to CMMC guidelines to protect sensitive data properly.
Is it possible to achieve CMMC certification on my own?
Going it alone with CMMC compliance can be tough because the framework is complex and detailed. Without expert help, you might miss critical security controls, risking non-compliance and losing contracts. Professionals can thoroughly assess your current cybersecurity, find gaps, and efficiently implement necessary measures. They also assist with documentation, audits, and continuous monitoring, saving you time and resources while ensuring strong protection of CUI. Partnering with experienced professionals increases your chances of successfully achieving and maintaining CMMC compliance.
When considering the ROI on your cybersecurity and compliance investment, it’s smarter to use a team with a proven success record rather than hiring full-time staff and buying costly solutions that might not work.
What does DFARS 7012 say about the requirement for FedRAMP-compliant cloud computing?
DFARS Section 252.204-7012 (DFARS 7012) requires DoD contractors using external cloud service providers to store, process, or transmit CUI to ensure these providers meet FedRAMP Moderate baseline requirements. FedRAMP (Federal Risk and Authorization Management Program) ensures that cloud services used by the federal government have strong security measures. By complying with FedRAMP, contractors meet the strict cybersecurity standards outlined in DFARS 7012, protecting sensitive defense information. This regulation highlights the importance of using verified and secure cloud services to safeguard national security interests.
What is the difference between CMMC and NIST SP 800-171?
While NIST SP 800-171 provides specific security controls for CUI protection, CMMC is a certification process evaluating the maturity level of an organization in meeting those requirements. CMMC also includes practices related to incident response planning, execution, and reporting.
Which Microsoft Azure and Microsoft 365 do I need to meet CMMC requirements?
The differences among Microsoft Commercial, Government Community Cloud (GCC), and GCC High are as follows:
- Commercial:
- Meets FedRAMP Moderate criteria.
- Uses the global Microsoft network, so data hosting locations and access by foreign nationals are unspecified.
- GCC:
- Similar to the Microsoft Commercial cloud but with specific identity measures and US hosting requirements.
- Not adequate for ITAR because foreign nationals could have infrastructure access.
- GCC High:
- A separate cloud environment with US-based personnel and hosting.
- Required for organizations with ITAR requirements.
- Lacks some features of the commercial cloud.
For CMMC compliance, if you don’t have ITAR-related requirements, the Commercial or GCC versions may suffice. However, if you need to comply with ITAR, you must use GCC High.
What 3 things do you need to get CMMC certified?
To get CMMC certified, you need the following three things:
- SPRS Score: Submit your Supplier Performance Risk System (SPRS) score, which reflects your compliance with NIST 800-171 requirements, to the Department of Defense.
- SSP (System Security Plan): Develop and maintain a comprehensive System Security Plan (SSP) that outlines your current cybersecurity practices and how you address CMMC requirements.
- Assessment Score: Undergo an assessment by a certified third-party assessor to evaluate your compliance with the CMMC requirements and achieve the necessary assessment score for certification.
These components ensure your organization’s readiness and compliance with CMMC standards.