Making digital peace of mind accessible.
Comprehensive cyber defense and compliance for mid-market companies.
We are an expert managed GRC services provider.
Mitigating Insider Threats in the Age of AI
Trusted Experts, Recognized Accomplishments

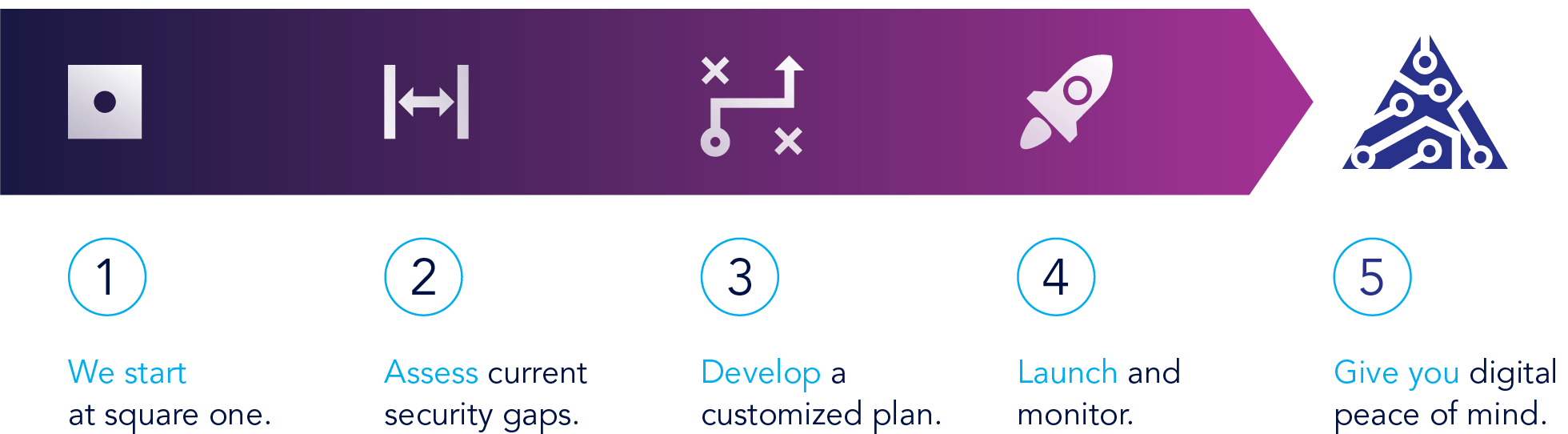
We Meet You Where You Are
Building on your existing foundation, we align solutions to your business goals and provide ongoing management for long-term success.
Why Customers Choose Abacode
“[Abacode] took care of everything from implementation of 24/7 Security Operations Center Monitoring, to identifying the CMMC 2.0 gaps and risks… helped our business mature and grow, and that is why we continue to rely on them for our cybersecurity and compliance needs.“
“Abacode aligned our firm’s cybersecurity program & SOC 2 Type II compliance need to deliver ultimate value to our organization.“
“Abacode was the first company that could not only advise our team on the right strategy but also implement and run an entire outsourced Cybersecurity and Compliance program for us.“
Delivering Outcomes That Matter
| Predictable Security Outcomes |
| Optimize to defend against new threats |
Align to operational resilience for business continuity |
Improve cost efficiency and reduce complexity |
| Compliance-Driven Business Outcomes |
| Create a competitive advantage |
Comply with data protection and privacy regulations |
Enhance customer trust and reputation |
Schedule a Consultation
We will help you understand what you need to achieve your security goals.

Get CMMC Ready
Enabling DoD contractors to confidently meet and maintain CMMC compliance.
As a Cyber AB Registered Provider Organization (RPO), we help ensure your organization’s audit readiness through a comprehensive program and our team of in-house CMMC experts.
Abacode has successfully prepared and navigated CMMC Level 2 assessments for our clients from both a C3PAO and DIBCAC/C3PAO through the JSVA program.
We have a diverse clientele with the Defense Industrial Base (DIB): electronics and wiring components, packaging and distribution, mechanical components for aircraft, etc.
Our credentials as a managed CMMC compliance provider
-
U.S. Based Team
100% U.S.-based team, W2 employees.
-
Verified employees
100% E-verified background checks on all employees.
-
Cyber AB RPO
Cyber AB Registered Practitioner Organization (RPO) for CMMC.
-
C3PAO's
Established relationships with top Certified Third-Party Assessment Organizations (C3PAO).
-
GCC High & ITAR
Secure operations within GCC High environment & ITAR for confident monitoring.
-
SRM
Shared Responsibility Matrix available upon request.
-
SOC 2 Type II
SOC 2 Type II certified.
-
ISO 27001
ISO 27001 certified.
Start your CMMC journey today
We will help you with becoming compliant and maintaining the certification.
Abacode Achieves Certified Microsoft Solutions Provider
Designation for Proficiency in Security
Microsoft Security
Unlock the Benefits of your Microsoft Security Stack with Abacode