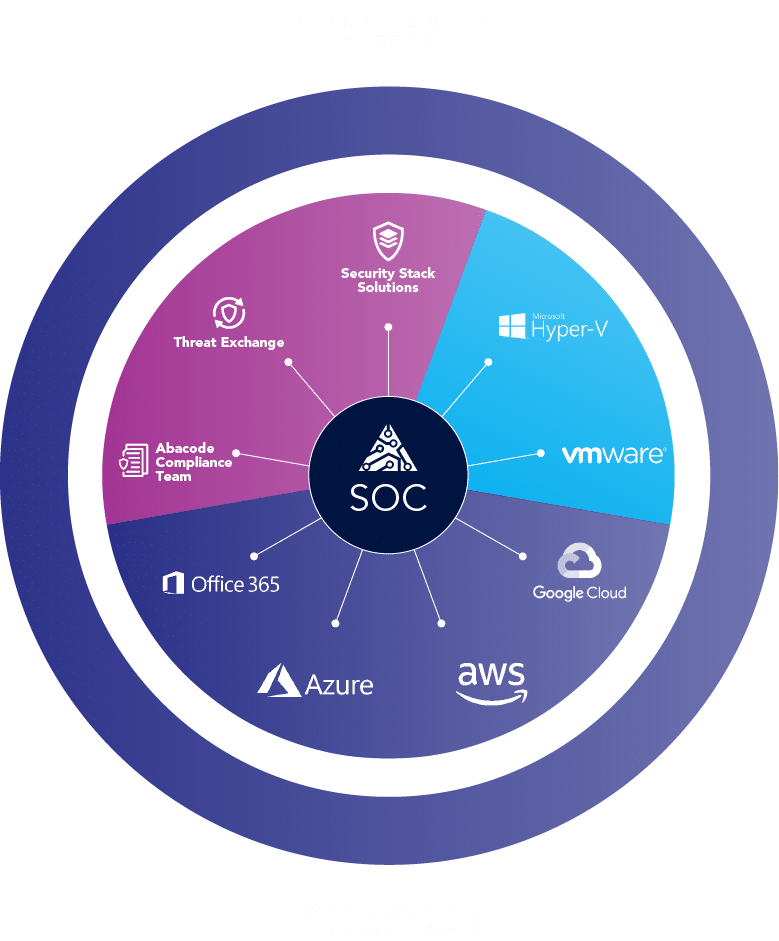
Your environment monitored and managed, 24/7/365.
Your business deserves protection that never sleeps. Our experienced security analysts monitor your environment 24/7, quickly identifying real threats while filtering out false alarms. With proven expertise in threat detection and response, we keep your operations secure so you can focus on what matters most - growing your business.
How is our Managed Security Operations Center unique?
-
People
- 24/7 Eyes on Glass cybersecurity monitoring services
- Tier 1, 2 and 3 SOC analysts collaborate in the analysis and triage of every detection
- Experts with leading Engineering and Security certifications including CISSP, CompTIA Security+, CySA+, Microsoft Security certifications and more
- Dedicated Customer Success Managers that drive best-in-class customer satisfaction
- Board-level SOC reporting including performance matrix and forward-looking security posture recommendations
-
Process
- Application of AI-driven detections and threat intelligence
- MITRE-ATT&CK-based detection and escalation lifecycle
- Enterprise-wide scope including on-premises environments, endpoints, cloud systems, and SaaS
- Root Cause Analysis that results in improved cybersecurity posture and reduction of noise
- Customer-specific playbook aligned with customer’s use cases, priorities, and preferences
-
Technology
- Strategic guidance and configuration of in-house technology and market-leading security technologies to meet customers at any level of their cybersecurity journey
- Secure operations within GCC High environment to confidently monitor customers working with the Department of Defense (DoD)
- Real-time access to case management and monitoring solutions for transparency and oversight
Why Choose A
Managed SOC?
Cost
Operating an in-house SecOps team is a large cost – between headcount, tech stack and training. Our Managed SOC gives you a team of experts that can help optimize your current or future tech stack, at a fraction of the cost.
Evolution
Modern IT teams are not currently built to combat the ever-evolving threat landscape – managed SOC monitoring increases and improves response time, monitors efficiently and accurately escalates relevant threats.
Talent
There is a massive shortage in talent for cybersecurity experts. According to the WEF, there is a 4 million shortage in cyber professionals.
Detect – Respond – Secure
-
Detect
24/7/365 managed SOC coverage and monitoring of your system backed by leading technologies optimized to identify and qualify true threats and anomalies. We don’t just monitor, we ensure your security operations run efficiently – saving you time and money.
-
Respond
Through constant learning and customizations, our security experts and analysts understand the business needs of your company. Our tiered analysts are trained to identify and escalate as appropriate – all based on your business needs.
-
Secure
Our security experts work with you on a customized gameplan based on your business needs and provide you the steps needed to be taken when an event happens to provide proper prioritization of the issue.
Take control of your cybersecurity — without the complexity
Organizations are now challenged more than ever to detect breaches at lightning speed, comply with rigorous standards, diligently assess vulnerabilities in their vendor chain, and grapple with surging cyber insurance premiums. Abacode Cybersecurity and Compliance can help partner with businesses to increase security posture and scale at a much lower cost than building out a team internally. Reach out to Abacode and we can discuss how we can help.
-
24/7 Managed SOC
Advanced Threat Response
Our world-class 24/7/365 “Eyes on Glass” Managed Security Operations Center (SOC) service stands as a testament to cutting-edge cyber defense, ensuring continuous and meticulous surveillance.
We integrate cutting-edge SIEM and AI Threat Detection software with our SOC, providing real-time visibility across your threat landscape and proactive threat management.
Every moment of every day, our dedicated professionals vigilantly monitor and act to protect your business from bad actors and compliance mishaps.
Secure your Business Now
Who Benefits from a Managed Security Operations Center (SOC)?
Small and Medium-Sized Enterprises (SMEs)
SMEs often lack the resources to establish an in-house SOC. A managed SOC provides them with 24/7 monitoring, threat detection, and incident response without the need for significant upfront investment.
Startups
Startups need to focus on growth and innovation, not cybersecurity. A managed SOC allows them to offload security responsibilities to experts, ensuring their data and systems are protected while they concentrate on their core business.
Manufacturing and Industrial
Manufacturing and Industrial companies are more susceptible to cyber threats due to their complex structures, legacy technologies and ever-evolving threat landscape. Combined with new regulatory frameworks for companies working with the DOD like CMMC – a managed SOC can help maintain compliance and safeguard IP, CUI and customer data.
Healthcare Organizations
With the increasing threat of cyberattacks targeting sensitive patient data, healthcare organizations can benefit from a managed SOC to ensure compliance with regulations and protect patient information.
Highly-Regulated Industries
A Managed SOC would benefit any organization in an industry that is or is in the process of being highly regulated. As the main threat detection or an auxiliary to your current SecOps, a managed SOC provides comprehensive coverage to strengthen adherence to a given framework.
Educational Institutions
Schools, school districts and universities handle a vast amount of personal data and intellectual property. A managed SOC helps them maintain robust security measures to protect this information, and their students information, from cyber threats.
Financial Institutions
Banks and financial services firms require stringent security measures to protect financial transactions and customer data. A managed SOC provides continuous monitoring and rapid response to potential threats.
Companies with an in-house SOC
Even if a company has an in-house SOC, they may not have the ability to monitor 24/7, 365 days a year. A managed SOC provides more coverage and less overworking of in-house analysts.
Committed to Compliance