The full view of your external risk environment.
Third Party Risk Monitoring (TPRM) through a seamless digital experience.
Streamlining Third Party Risk Monitoring
Current third party risk management methods are fragmented, manual, and often inaccurate. SCOUT consolidates and streamlines the process, reducing false positives, providing continuous risk visibility, and ensuring a proactive, real-time approach to third party security.
-
Increased Vulnerabilities Through Third Parties
Third Parties often have access to sensitive information and critical systems, making them potential entry points for cyber-attacks. Third party risk and supply chain breaches are among the top factors increasing the cost of a breach, according to the 2024 IBM Cost of a Data Breach Report. Operationally, any disruption or failure on the part of the Third Party can directly impact an organization’s ability to deliver products or services.
-
Ensure Your Third Parties Are Assets, Not Liabilities
SCOUT combines third party provided data, external threat intelligence based on four main risk areas (24 threat attributes total), and historical data to generate dynamic security risk scores. This allows organizations to mitigate security gaps with all Third Parties – instilling confidence that they strengthen, not weaken, your business.
SCOUT™
The full view of your external risk environment
Easy-To-Use Platform with Clear Insights
SCOUT features a centralized dashboard showing third party risk overview, customized and automated Question & Questionnaire Bank, third party assessment completion tracking, and auto-generated questionnaire-based risk score.
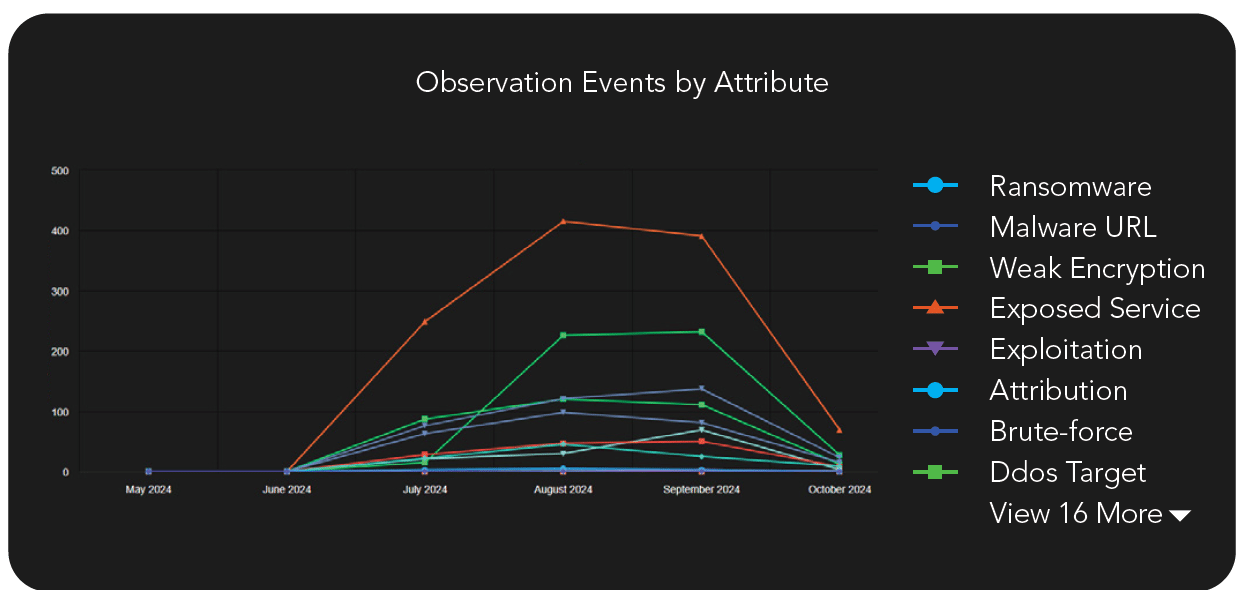
Threat Attributes Observation Graph
View 6 months of trending data observing 24 threat attributes to determine if findings are being addressed over time.
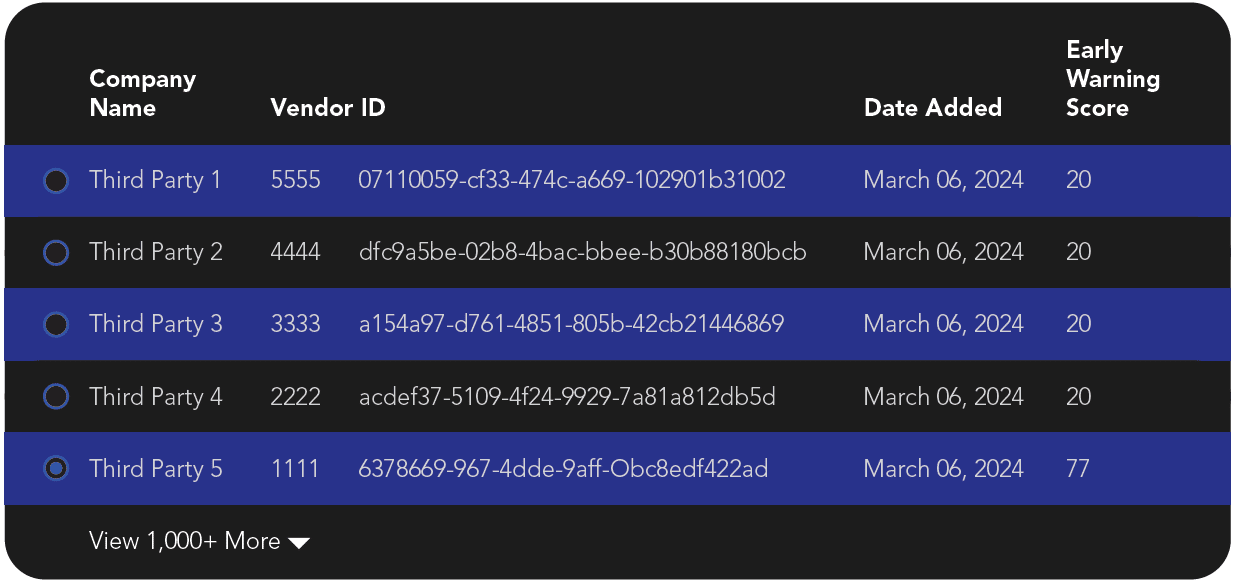
Comprehensive Third Party Risk List
A list view of all Third Parties and the ability to individually view their risk score, risk history, and threats associated with their domains.
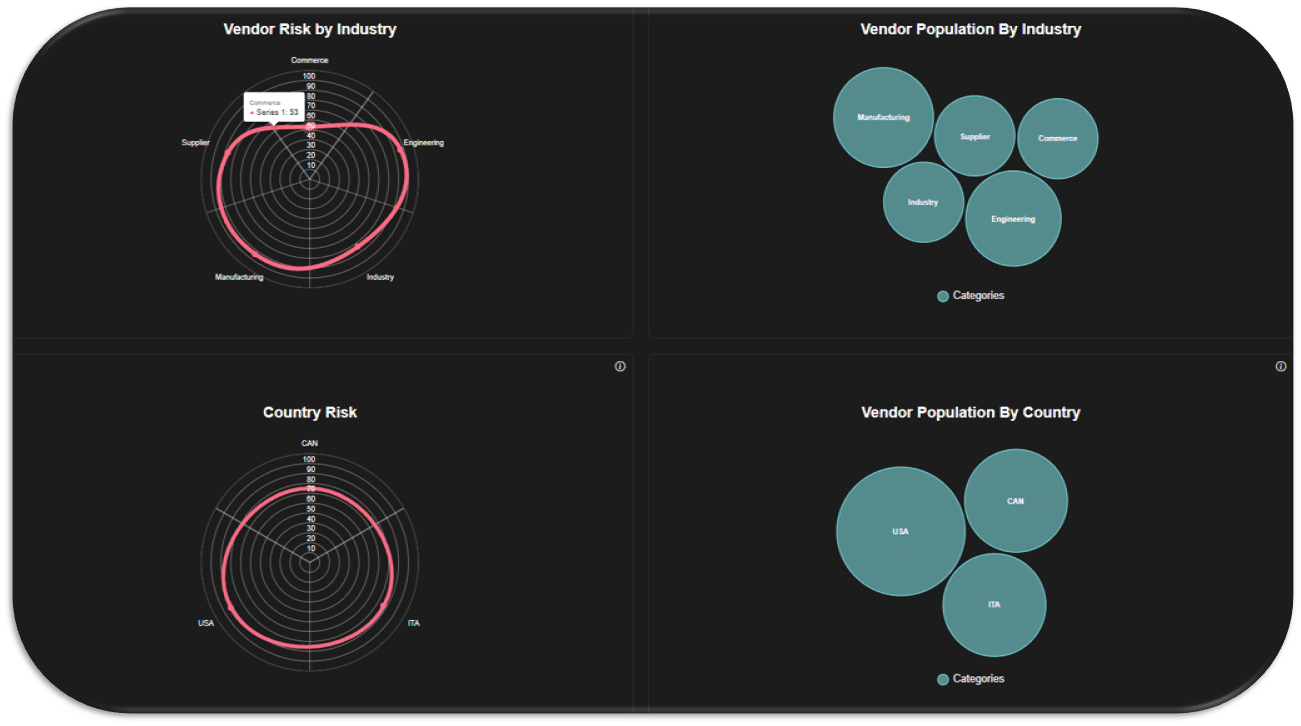
Vendor Demographic Charts
Access aggregated vendor scores, location data, risk by industry and country, distribution of risk scores, and track vendor risk trends on the vendor security page.
Find out how your Third Parties score today.
Abacode’s proprietary SCOUT technology allows organizations to understand and monitor the risks external parties may pose to them.
Innovative Technology meets Managed Services
Watch Video
Ensure Compliance with Top Frameworks
Stay compliant with leading frameworks that require third-party assessments and/or management
Your Solution for Third-Party Risk
Connect with an Abacode Solutions Advisor about SCOUT™ today















